There is a lot of hoo-ha recently about switching to TLS 1.2....
Well, mainly, the sound comes from Acumatica marketing team and also from some of those "security advisers", reviewing for us what is secure and what is not.
So, here is the proposed way to enable TLS 1.1 and/or TLS 1.2 on your IIS server.
And also proposing a way to make sure (or monitor) that your dear clients are connecting their browsers using secure protocols.
What we need to do first is to disable insecure protocols and enable secure ones.
Adding TLS 1.1 and/or TLS 1.2 to your server
If you wish to add just TLS 1.2 please download a file and add registry information to your IIS SERVER, here is the example of the file from Rahul Kumar's blog:TLS 1.2 ONLY
You can also manually create reg file with this content. Please Note that this will also disable some less secure protocols like SSL 2.0, SSL 3.0, TLS 1.0 and TLS 1.1:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
If you wish to leave TLS 1.1 enabled, please use another script instead:
TLS 1.1 and 1.2
Content would be like below, if you prefer to create .reg files manually:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
There could be an issue with FIPS enabled in your system, if .NET throws an error that:
"This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms."
All you need to do is to disable FIPS under Local Security Policies.
Disabling FIPS under Local Security Policies
1. Open Control Panel, click Administrative Tools, and then double-click Local Security Policy.
2. Under Local Security Settings, expand Local Policies, and then click Security Options.
3. Under Policy in the right pane, double-click System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing, and then click Disabled.
4. Run gpupdate /force
Monitoring the client communications protocol
This is the best part actually. After you enabled TLS 1.2 it is time to show the auditors that you are compliant 100% with what is called security. Today. So we may have IE, FireFox and Chrome.
Check the security protocol used on Internet Explorer
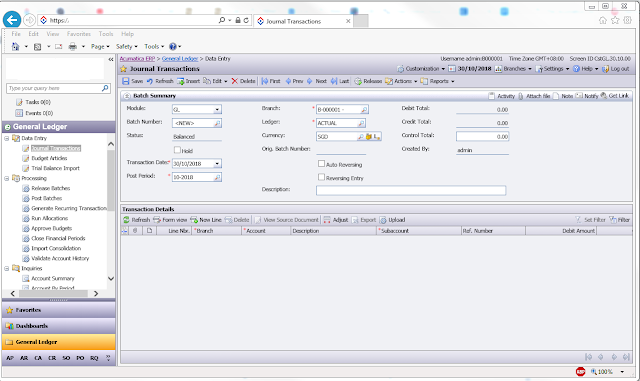
First you need to connect to your Acumatica using IE. I am demonstrating customer who is using Acumatica version 3.0. And, yes, 3.0 also supports TLS 1.2. Please note it should be HTTPS protocol of course:
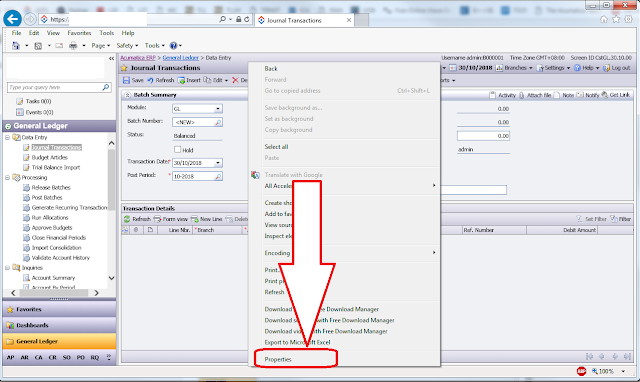
Secondly, right click on the header of the screen (do not right click on grid!) and you will see a choice drop down. Click Properties:
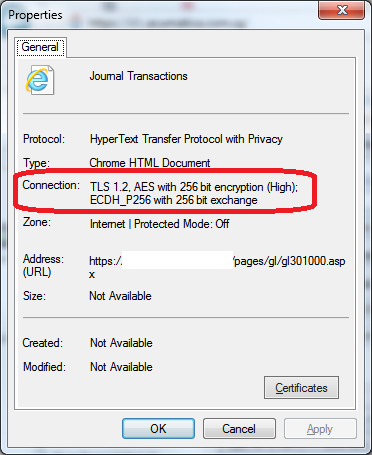
Third, check the Connection.
Check the security protocol used on FireFox
Login, Click on (i) option, list to second page, enjoy
Click on this arrow > and you will see option then click More Information
 |
Then you will see detailed info
Check Security protocols used on Google Chrome
Here you need to press F12 and then choose Security option:
Sergey.



After enabling TLS 1.2 on the server is there any changes needed on the acumatica web service connection code.
ReplyDeleteWe have an application which is using acumatica Web Services to connect to acumatica and retrieve the data but since we have enable TLS 1.2 on the server the application is not able to connect to the Acumatica web service.
Does Acumatica has updated the web service connection code for TLS 1.2 do you have any suggestion for this please let me know.
Thanks in advance
Hi Abdul, I understand you used HTTP web service, not what to switch to HTTPS? Or once TLS 1.2 enabled your HTTPS stopped working? As far as I remember .NET has limitations on TLS, therefore if you are using Acumatica version 3 then yes there will be issues.
Delete